- “여러 AI 모델을 로컬에서 테스트 가능”···구글, 오픈소스 앱 ‘AI 엣지 갤러리’ 공개
- Why I recommend this OnePlus phone over the S25 Ultra - especially at this new low price
- I replaced my laptop with Microsoft's 12-inch Surface Pro for weeks - here's my buying advice now
- This palm recognition smart lock doubles as a video doorbell (and has no monthly fees)
- Samsung is giving these Galaxy phones a big One UI upgrade - here's which models qualify
Websites Hosting Fake Cracks Spread Updated CopperStealer Malware

Malware
We found updated samples of the CopperStealer malware infecting systems via websites hosting fake software.
June 17, 2022
Read time: ( words)
We noticed a new version of CopperStealer and analyzed these samples to be related to a previous campaign we’ve documented. We examined this new version reusing parts of code and observed the following similarities from previous versions:
- The same cryptor
- Use of Data Encryption Standard (DES) with the same key
- The same name of the DLL export function (for later versions of CopperStealer)
- Data exfiltration to a Telegram channel (for later versions of CopperStealer)
- Use of the executable utility MiniThunderPlatform
First Stage: Cryptor
We observed CopperStealer‘s binary being encrypted and appended to a legitimate application with its entry point overwritten by a shellcode. This shellcode reads an offset of the payload and XOR decryption key from the executable file header, which is the same method that we described in our report.
As highlighted in the screenshot, the encryption key is 0x001eb1c0, which is 2011584 in decimal. The decimal value is both the offset and the encryption key. All the samples we analyzed use the same scheme. The following screenshot shows the beginning of the encrypted data. The decryption is an XOR function with the same key as offset in decimal.
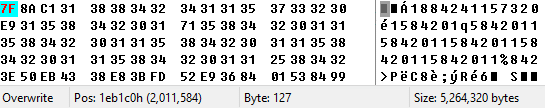
The decrypted second stage is an Ultimate Packer for Executables (UPX)-packed DLL and has one exported function called HelloWorld. It’s important to note that in older versions of CopperStealer, this was called WorkIn, while newer versions already had HelloWorld.
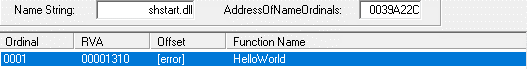
Second Stage: Dropper
We analyzed the second stage as a dropper embedding two additional executables (compressed with 7-Zip), internally named A and B. These resources are dropped under the names “build” and “shrdp” and subsequently executed. We looked into their component functions as “browser stealer” and “remote desktop”.
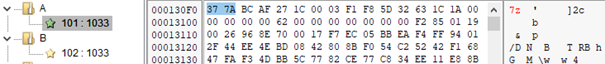
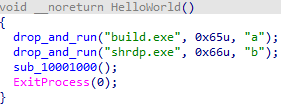
First component: Browser stealer
This component uses the same payload encryption technique and the same export method name as the routine discussed in the first stage. The component installs a certificate with a thumbprint 6c0ce2dd0584c47cac18839f14055f19fa270cdd in the Certificates folder of the current user. The same certificate is mentioned in the indicators of compromise (IOC) section of another report and is also assigned to CopperStealer.
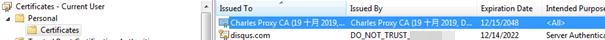
The browser stealer then extracts a “MachineGuid” value from <Software\Microsoft\Cryptography> and uses this string value as the name of the directory where it stores all the stolen data. It then searches for and steals cookies from the following browsers:
- Brave-Browser
- Chrome
- Chromium
- Edge
- Firefox
- Opera
- Yandex
The cookies in Chromium-based browsers are encrypted. For that purpose, the stealer reads os_crypt and encrypted_key from the <%APPDATA%LocalGoogleChromeUser DataLocal State> file, decrypts the key, and stores its encrypted value. We analyzed this encrypted value to be base64-encoded, then DES-encrypted with key “loadfa1d” and IV “unsigned”, followed by another base64-encoding. This encrypted and encoded value is then saved to a file named <%APPDATA%LocalGoogleChromeUser DataHistory>.
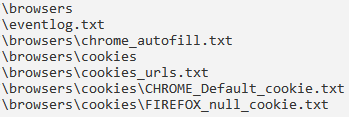
The stealer starts taking the data, creates directories labeled “browsers” and “cookies” in the directory named MachineGuid, and stores the stolen data in the said directories based on the file content. These file names are self-explanatory of the data stolen from the infected system, as follows:
- passwords.txt
- passwords_urls.txt
- _cookie.txt
- cookies_urls.txt
- CC.txt
- chrome_autofill.txt
- _token.txt
- outlook.txt
- thunderbird.txt
- eventlog.txt
Aside from stealing web browser data, the stealer also gathers user data from online messenger platforms Telegram, Discord, and Elements, game distribution service Steam, and email clients Outlook and Thunderbird. The stealer copies all the important files with settings and configurations and sends them back to the command-and-control (C&C) server:
- Telegram: The stealer scans for “tdata” folder wherein all data such as sessions, messages, and images are stored.
- Discord: It looks for “userDataCache.json” file.
- Elements: It looks for “IndexeDB” directory where the messenger app stores information such as access tokens.
- Steam: It searches for “config” file with the settings in a number of locations being discussed here.
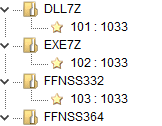
Firefox stores its saved logins encrypted in a logins.json file. The stealer contains a resource utility called FFNSS332 for a 32-bit system (or FFNSS364 for a 64-bit system), which parses the logins.json and prints its results on the command-line output. We also noticed embedded files DLL7Z and EXE7Z, which contain all the stolen data in one archive compressed with 7-Zip.
The stealer runs a Windows Events Command-Line Utility and lists the dates of events 6005 (when the event log service was started) and 6006 (when the event log service was stopped), and saves these output to eventlog.txt file. The entire directory of stolen files is compressed into a password-protected 7-Zip archive (wherein 7z.dll and 7z.exe are included as resources), and the archive password is md5[duplicated directory name]. The archive is then uploaded to a dedicated Telegram channel and a message about a successful upload is sent to the notification channel.
Second component: Remote desktop
Similar to the first component, the second component uses the same payload encryption and the same export method naming convention as explained in the first section.
This component starts to decrypt the C&C server address, stored in an encrypted form on Pastebin. After a base64 decoding, the decryption algorithm is DES with keys “taskhost” and IV “winlogon”. This is exactly the same settings mentioned in our previous CopperStealer analysis. After the C&C address is obtained, the component registers its machine identifier (under the value “MachineGuid,” the same identifier in the first component) and periodically starts querying for tasks to be performed.
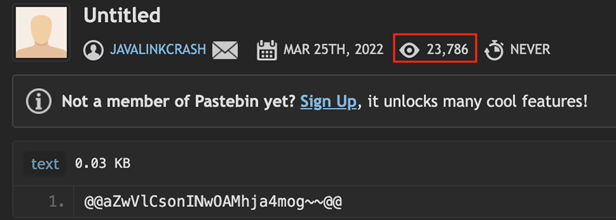
Following this finding, we looked into the account responsible for sharing this on Pastebin. The account’s name is Javalinkcrash, and it was created with only one paste with the encrypted C&C server address. According to the statistics provided on the detailed view, the paste was created on March and has garnered more than 23,000 views as of this writing. We believe the view number could be an estimate of the number of victims infected with this new variant of CopperStealer.
The supported tasks are “install” and “killme”. The “install” task performs the following operations:
- Adds a new user account to the machine, wherein the password is the same as the username
- Adds this user account to the administrators’ group and “Remote Desktop Users” group
- Hides this account from the login screen by modifying the <\Winlogon\SpecialAccounts\UserList> registry key
- Disables the firewall
- Allows remote desktop connections.
- Disables Network Level Authentication
- Extracts and installs RDP wrapper (named as “SHRDP” in resources), derived from the rdpwrap project and once installed, enables the Remote Desktop function on its host system
- Extracts and installs OpenVPN (drivers and certificate, OEMVISTAxxx, and TAPxxx in resources + OP in resources).
- Extracts and installs MiniThunderPlatform (named “THUNDERFW” in resources), another utility that we also mentioned in our previous analysis of CopperStealer
- Extracts and installs n2n (named as “EDGE” in resources), a tool for creating virtual networks (The execution parameters “-k”, a secret encryption key, “-a”, a private IP address, and “-l”, a supernode IP and port, must be received from the C&C server.)
The “killme” task kills the running processes, deletes files, and removes the users that were started, dropped, or added during the “install” task. All the Remote Desktop-related files are also supplied in resources and the component simply extracts and installs them.
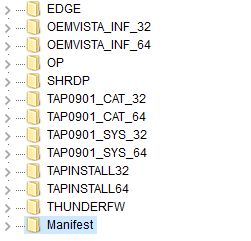
To prevent Windows Defender from detecting the dropped files, the component adds the directory in the exclusion list.

Infection vector
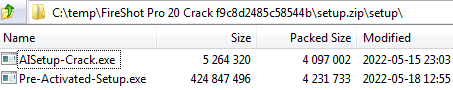
Similar to the previous analysis of CopperStealer, the infection vector starts with a website offering fake cracks. These websites usually display two buttons, one offering to download and the other to set up the desired cracks. Selecting either button begins the redirection chain, requiring the user to select another “Download” button. Afterward, a download prompt appears and the user is prompted to save the file to the computer.
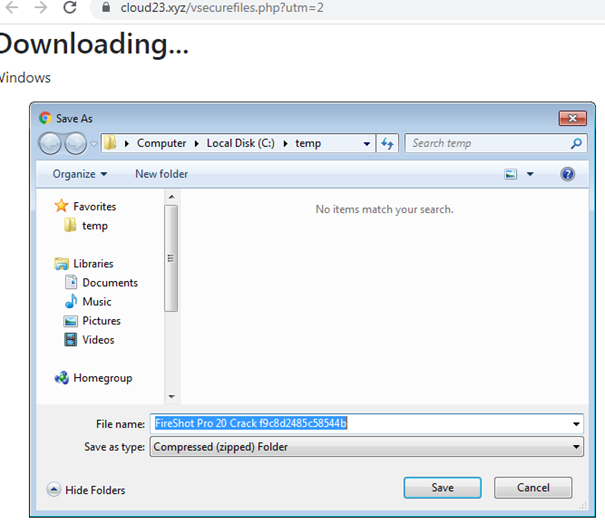
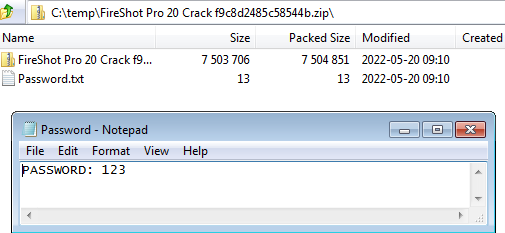
To prevent security solutions from immediately detecting the malicious files, the downloaded archive usually contains a text file with a password and another encrypted archive. After the password mentioned in the text file is entered, the decrypted archive shows the executable files. In this sample, there are two files CopperStealer and Vidar Stealer.
Additional findings
Aside from the updated malware, we noticed that the operation of CopperStealer’s C&C infrastructure has also changed. The previous CopperStealer’s communication leveraged Domain Generation Algorithms (DGA) to randomize its C&C domains and abused the content delivery network (CDN) proxy to hide the real IP address of the C&C server. The DGA and CDN proxy help the stealer increase the stability of its network communication and help avoid detection from network protection solutions of its C&C domains and IP addresses. However, a collaborative sinkhole operation of threat researchers and service providers disrupted CopperStealer’s previous infrastructure.
Likely due to the disruption, CopperStealer’s infrastructure is now constructed differently. The C&C is no longer generated with DGA; rather, it is specified with an encrypted configuration hosted on a third-party webpage (in this sample, Pastebin was abused). Instead of using a CDN proxy, we found that its C&C domain adopted a fast flux DNS service provided in the underground forum. The fast flux DNS service could switch CopperStealer’s C&C domain between different IP addresses every few hours and add a layer of proxy to protect its C&C server. While the technique is not new, we observed the switch occurring up to two times per day on a daily basis.
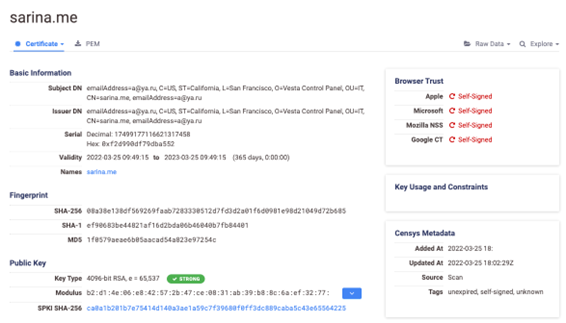
With the help of search engine Censys, we identified the real IP address of the C&C server that was hiding behind the fast flux DNS service. The server has port 8443 open for C&C communications with the infected machines (as clients). It has other open ports, which are listened to using open-source hosting Vesta Control Panel (VestaCP). Upon looking into the associated certificates, we observed that while their organization name is “Vesta Control Panel,” their subject common name is different from the stealer’s C&C domain. The certificates also contain a distinct subject email address, “a@ya.ru.” By searching for this email address, we identified similar VestaCP servers hosted among multiple providers. We also noticed that some of these servers are used for hosting phishing websites and other C&C behavior. These details led us to believe that these servers were probably managed by a bulletproof hosting service for illegal purposes.
Conclusion
From the outset, organizations and users are highly discouraged from downloading cracks from third-party websites. Some unofficial sites host functioning software but can be attached with hidden and additional illicit components unrelated to the advertised functions. Moreover, fake software can potentially be abused for multiple attacks and infections, and data stealers like CopperStealer can be used by the attackers to take sensitive information for more illicit activities.
Moreover, despite CopperStealer’s basic capabilities for stealing data in infected systems via a dated technique, the development that involves using new platforms such as Telegram and redundant encryptions shows that the attackers themselves are learning to vary their evasion and communication procedures. From a functional perspective and at scale, this increases the consequences and impact of their infections financially.
Users are advised to keep their systems constantly patched and their security solutions updated. We also recommend enabling basic security detection and prevention solutions such as a firewall and antivirus prevention engines to protect systems from threats like CopperStealer.
Indicators of Compromise (IOCs)
You can find the full list of IOCs here.
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk

